Other Features
•Conditional Access on iOS ISAC Client
•Device Validation Support for VoD and Per-App VPN
•Collecting Log Files from Ivanti Secure Access Client for iOS
•FaceID for Secondary Authentication
•SAML as Secondary Authentication
Conditional Access on iOS ISAC Client
Conditional Access feature allows to use identity-driven signals as part of the access control decisions. Conditional access brings signals together, to make decisions, and enforce organizational policies. This feature allows administrators to restrict access to approved client apps using Intune app protection policies.
For detailed information refer What is Conditional Access in Microsoft Entra ID?
To enable conditional access:
- Configure a SAML cloud app on Azure IdP and Connect Secure. See, Deploying a BYOD Policy for Microsoft Intune Managed Devices (ivanti.com) and Client application configuration.
- Create Device Feature policy configuration in Intune MDM under Devices > Manage devices > Configuration > Create > New policy.
-
Under Device feature configuration, edit “Single sign-on app extension configuration" and add below three key value pairs:
Field
Value
Value Type
browser_sso_interaction_enabled 1 Integer AppAllowList net.pulsesecure.pulsesecure String disable_explicit_app_prompt 1 Integer -
Configure conditional access policy, See Plan a Microsoft Entra Conditional Access deployment.
-
Create Conditional access policy on Azure IdP.
- Select the user to apply the policy.
- Select the target resource.
- Choose conditions.
- Select Device platform as iOS for iOS devices.
- Select Client apps as Browser. Mobile devices use browser for login.
- Block or grant access to the resources based on the above conditions and device compliance state.
-
- Identity based restriction is configured from MDM.
- Conditional access policy gets applied based on the compliance state fetched from Intune MDM.
Device Validation Support for VoD and Per-App VPN
Apps can be configured to automatically connect to VPN when they are launched. Using this feature, only the corporate-managed apps will transfer the data over the VPN. Personal data of employees such as personal web browsing, and connections to gaming and social networks will not use the VPN.
When the VPN On Demand profile is applied to the device, VPN will be started automatically in the following two conditions:
•When the applications are launched.
•When the application sends traffic in the background.
In VPN On Demand, a blocking interface is set up on the device which monitors the configured apps for the network traffic. Whenever an application whose network access type is "require VPN" tries to perform any network activity, the blocking interface detects this. It thereafter authenticates the user, tears down the blocking interface, and establishes the VPN connection.
EMM Configuration
The configuration needed to be enabled on EMMs. Following Parameters should be configured by the EMM Vendor to set up a VPN On-Demand profile:
|
Parameters |
Value |
|---|---|
| AppVPN Action | 0 (To allow) 1 (To deny) |
| AppVPN Packages | CSV for package identifiers to Allow/Deny eg. com.chrome.android, com.android.dropbox |
| Authentication Type | 1 (Certificate Based) |
| Certificate Alias | The client certificate alias |
| Profile Name | Any |
| Route Type | 1 (Per App) |
|
URL |
ICS URL |
|
VPN Trigger Type |
1(On Demand) |
VPN On Demand Limitations
•No Support for FQDN based Split Tunneling
Device ID Validation
This feature allows to read Unique Device ID (UDID) from MDM application configuration and pass to Connect Secure. On validation, Connect Secure initiates authentication.
FaceID for Secondary Authentication
This feature allows FaceID/Touch ID to be enabled while using secondary Authentication.
TLS 1.3
ISAC supports TLS 1.3. To configure TLS 1.3, see TLS 1.3 support.
SAML as Secondary Authentication
ISAC supports MFA auth on Mobile client with SAML as secondary authentication. This feature enables ISAC Mobile client to connect to ICS profile where the Primary Authentication is certificate and Secondary Authentication is SAML.
Derived Credential Support
This feature provides certificate-based authentication support for classic L3 VPN profiles where certificates are installed and managed by another application. These applications install digital certificates in device keystore for Android, or the MDM appconfig for iOS, and replace the need of physical smartcards for authentication.
Ivanti secure Access Client 22.5R1 supports Ivanti Neurons for MDM (Ivanti EPMM and Ivanti MDM) and Entrust application as certificate provider.
Supported Platforms
•Ivanti Secure Access client 22.5.1
•PIV-D manager application
•Ivanti Mobile@Work 8.6/ Ivanti Go 3.1 for core and cloud respectively
•iOS 14 / Android 10 onwards
Configuration of Derived Credentials
The configuration includes initial setting up by admin and then end user enrolment.
1.Admin configures the CA root certificates, and the User certificates provided by the vendor in the MDM.
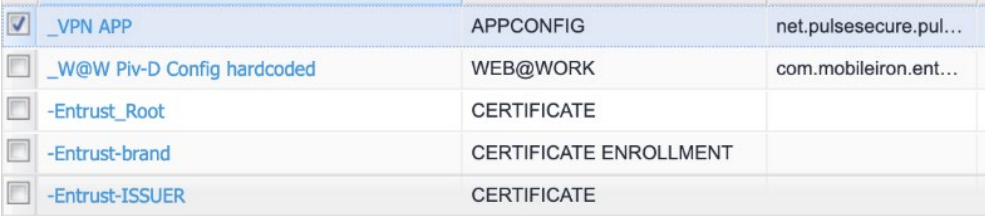
2.Admin adds appconfig policy to config ISAC client details in the MDM.
3.Admin installs corresponding CA root certificates on ICS for cert chain validation.
4.End user enrolls to MDM to fetch the appconfig policy.
5.End users browse the Entrust portal and select I’d like to enroll for a derived mobile smart credential.
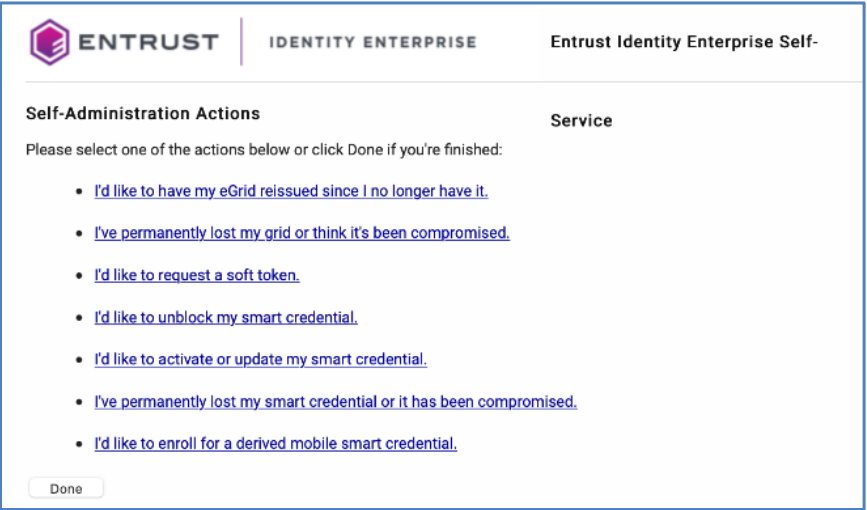
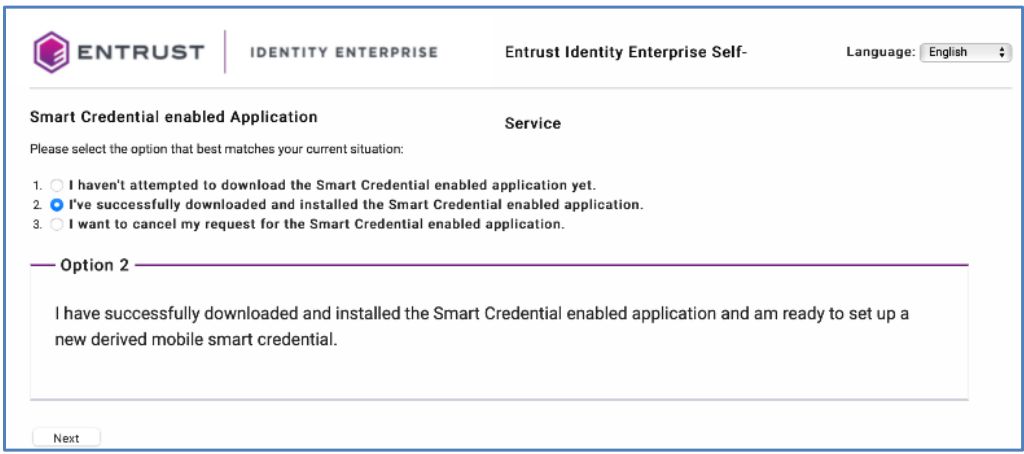
6.In the next screen, select the option I’ve successfully downloaded and installed the Smart Credential enabled application. Then click Next.
7.Enter the name for the derived credential and click OK.
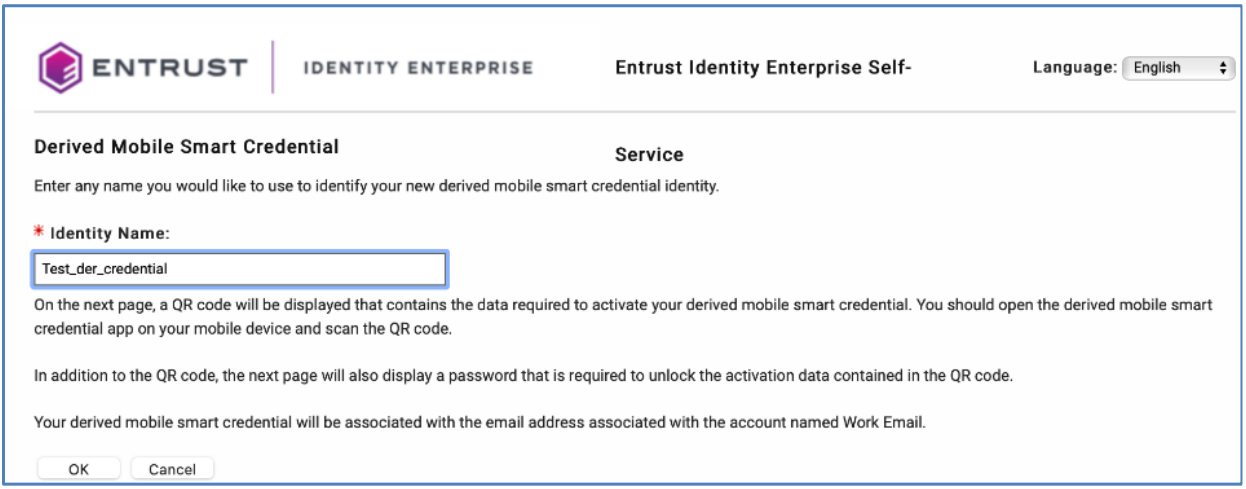
8.A QR code displays, use the PIV-D Manager application to scan and enter the password to install the certificates.
The certificates are installed in the MDM and ISAC fetches the user certificate from MDM client application.
VPN Configuration
One method of creating VPN configurations is to use a Configuration Profile to define Ivanti Secure Access Client configurations for the iOS device, and then distribute the configuration profiles by e-mail or by posting them on a Web page. When users open the e-mail attachment or download the profile using Safari on their iOS device, they are prompted to begin the installation process.
You use the iPhone Configuration Utility to create configuration profiles and specify Ivanti SSL as the Connection Type for the VPN Payload. You can download the iPhone Configuration Utility (3.0 or later) from the Apple support Web. For details about the utility and how to create Configuration Profiles, see the iPhone OS Enterprise Deployment Guide, available from the Apple website (www.apple.com).
Collecting Log Files from Ivanti Secure Access Client for iOS
The iOS device user can use the following procedure to e-mail the Ivanti Secure Access Client log files:
1.On the iOS device, start the Ivanti Secure Access Client app.
2.Navigate to Support > Share email or Share with other medium.
3.Enter an e-mail address, then tap Send.
Dark Theme Support
Ivanti Secure access client supports Dark mode or bright mode as per mobile settings.
Voice Over Support
Ivanti Secure Access Client supports voice over instructions as per mobile settings.
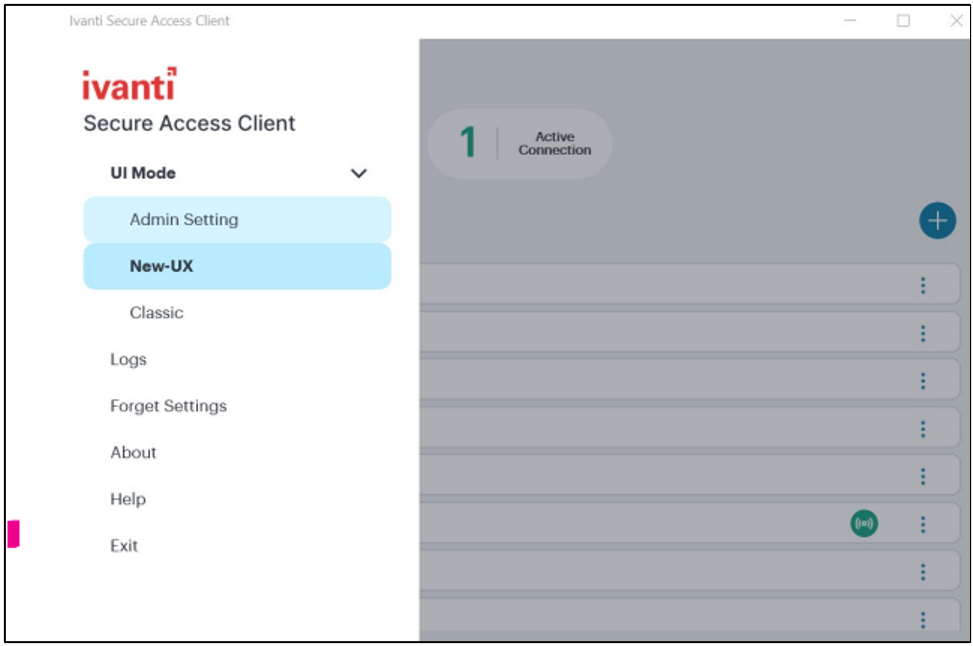
UI Mode Switching
Ivanti Secure Access Client supports switching between classic UI and New-UX. Use Menu and UI mode to switch between the modes.
.